Features
Veramine's intelligent sensor and advanced detection algorithms
detect common and sophisticated attacks
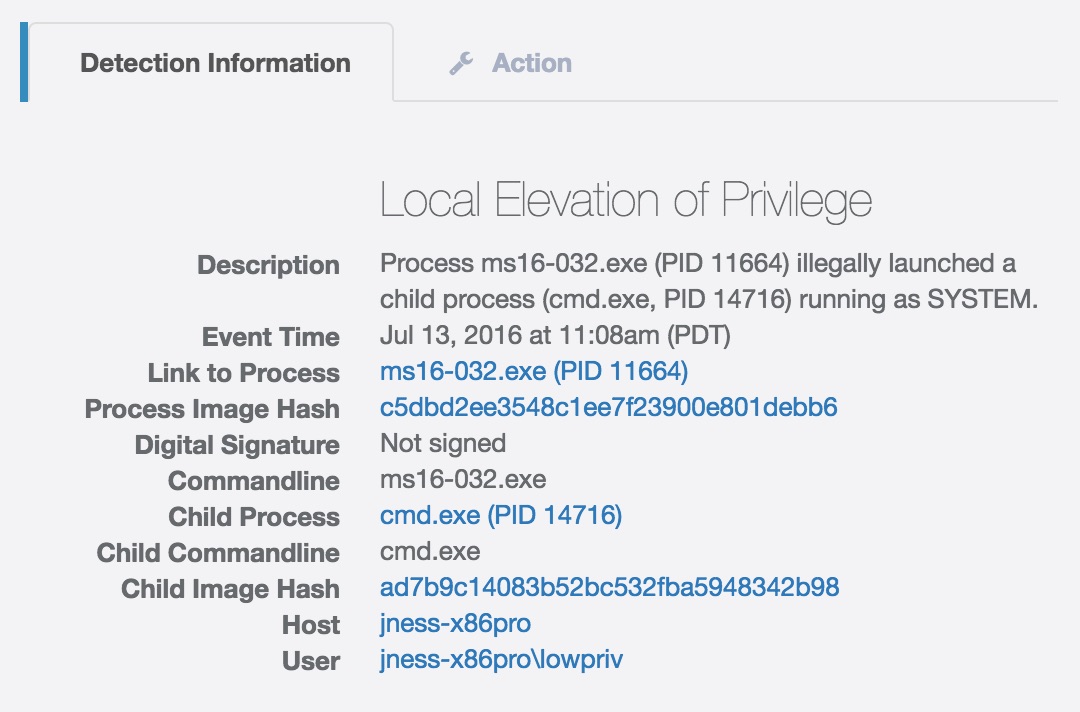
Kernel exploits
New Windows kernel 0day exploit in the wild? Our system can generically detect both known and unknown kernel exploits on all supported platforms!
Process migration and injection
More advanced attackers blend their malicious activities with normal system activities via remote thread injection. Our platform automatically tracks and detects such activities.
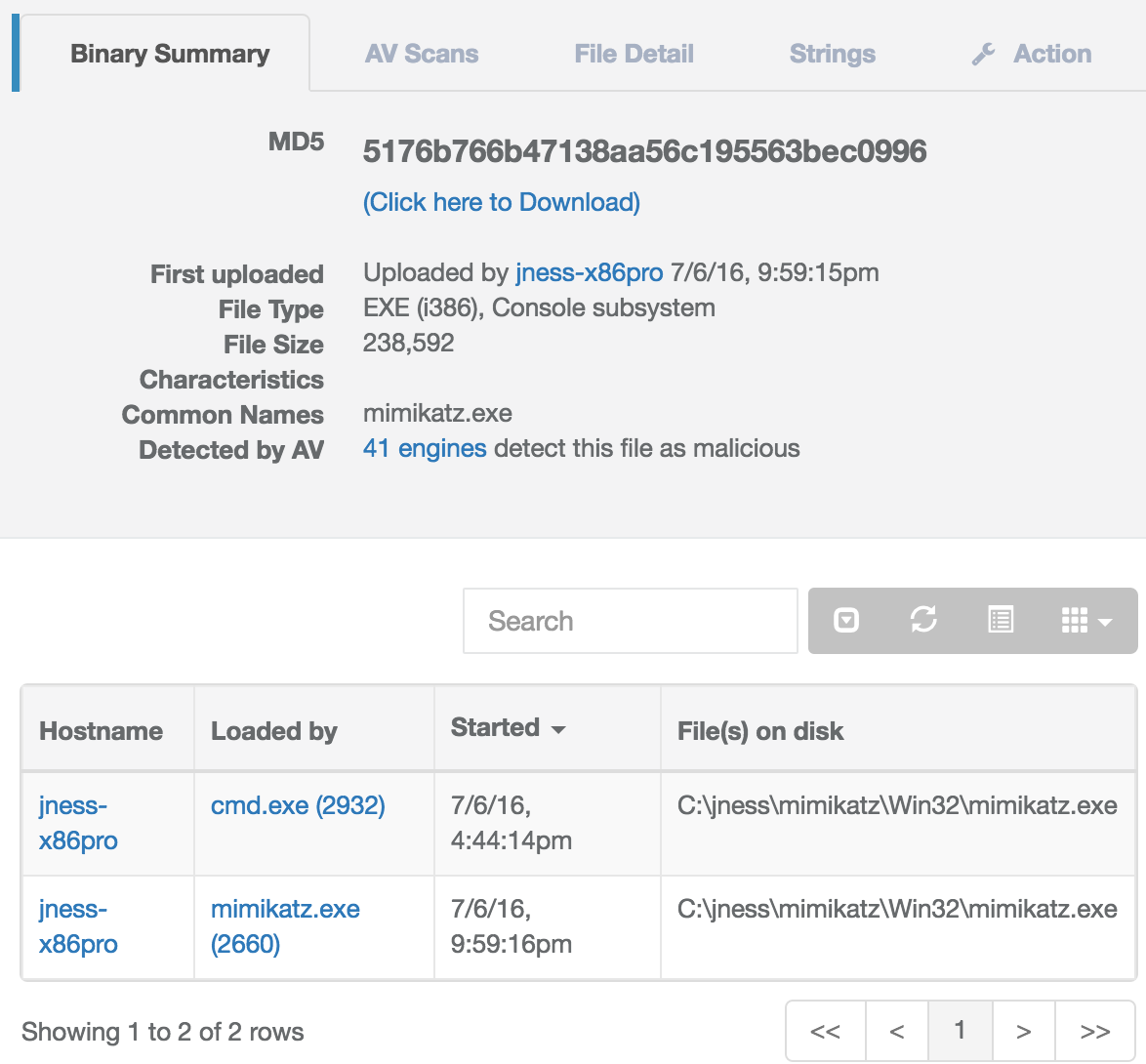
Credential dumping / pass-the-hash / lateral movement
Attackers commonly dump, collect, and reuse user credentials to gain further access in your network. We automatically detect these activities.
Download-and-run trojans
Want to know which users downloaded a "greetingcard.exe" from Outlook and executed it? We can instantly provide the answer.
Compliance
Ever wonder which users don't encrypt their HD? What about those who don't lock their machines or have a screensaver set? We can tell you the answer and save you money on the compliance audit and energy bill.
Tailored analysis
All data in our platform is fully searchable so you can slice and dice it as as you see fit. Want to process our data with your own Apache Hadoop or Spark analysis framework? We can stream the events to your system in real time.
Selected events stored forever
The Veramine free product displays the current day of activity. Our paid product allows browsing and search across as long a time range as the sensor is running.